Super Bowl LIX between the Philadelphia Eagles and the Kansas City Chiefs on February 9th, 2025, at the Caesars Superdome, was the eleventh Super Bowl to be held in New Orleans, and it was not the close affair we expected! In fact, the Eagles reached an insurmountable lead of 34 points before the Chiefs managed a first score. The event boasted record peak views of around 135 million, up from 124 million last year.
It was also a record-breaking 2025 in gambling terms, with significant growth in online betting compared to last year’s, reflecting the continued expansion of legal online sports betting in the US. An estimated $1.39 billion was gambled on Super Bowl LIX, up from $1.25 billion in legal bets for Super Bowl LVIII — a growth of about 11%. This figure marks the first time the American Gaming Association (AGA) based its estimate solely on legal wagers, unlike previous years that included illegal and casual bets, suggesting the actual increase in regulated online activity could be even higher as the market shifts toward legal channels.
This year also saw at least one $1m bet and a six-figure wager on the coin flip (tails by the way).
Continent 8 customer, FanDuel, reported record-breaking activity for Super Bowl LIX, with over 16.6 million bets placed by almost 3 million customers, a nearly 20% increase in bets from the 14 million recorded for LVIII (which totalled $307 million in wagers from 2.5 million users). In New York alone, a key online sports betting market, the Super Bowl LIX week saw a handle (total amount wagered) of over $557 million, with $155 million tied directly to the game, outpacing last year’s figures. FanDuel’s handle in New York for that week was $222.2 million, and DraftKings reported $193.9 million, both reflecting robust growth.
As the largest network, infrastructure and cybersecurity supplier to the US and global regulated iGaming market, Continent 8 can report its stats for Super Bowl LIX:

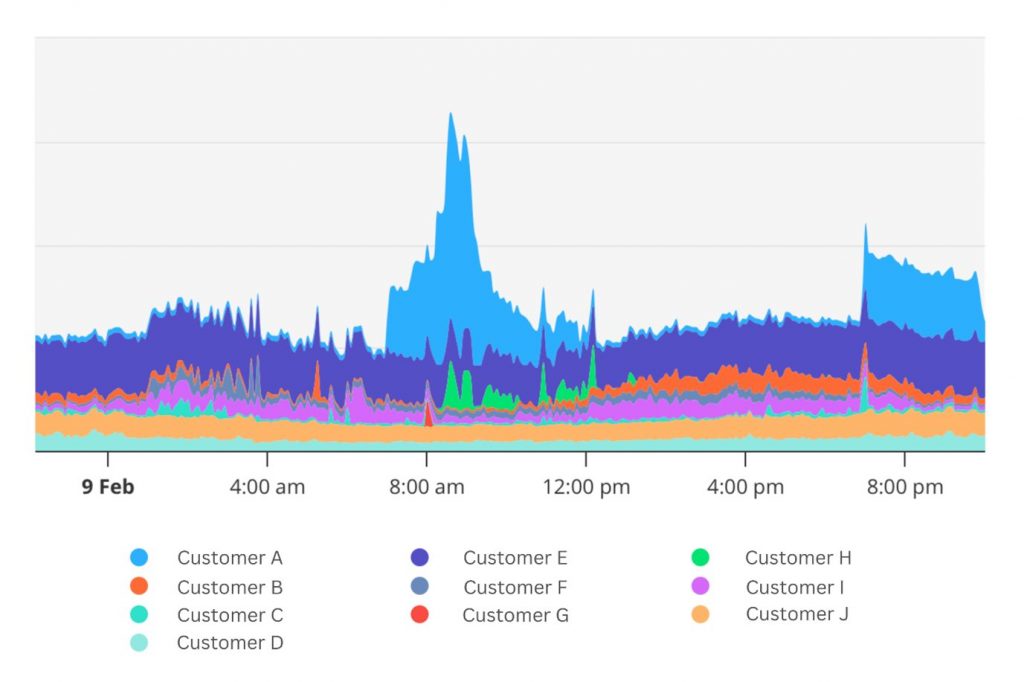
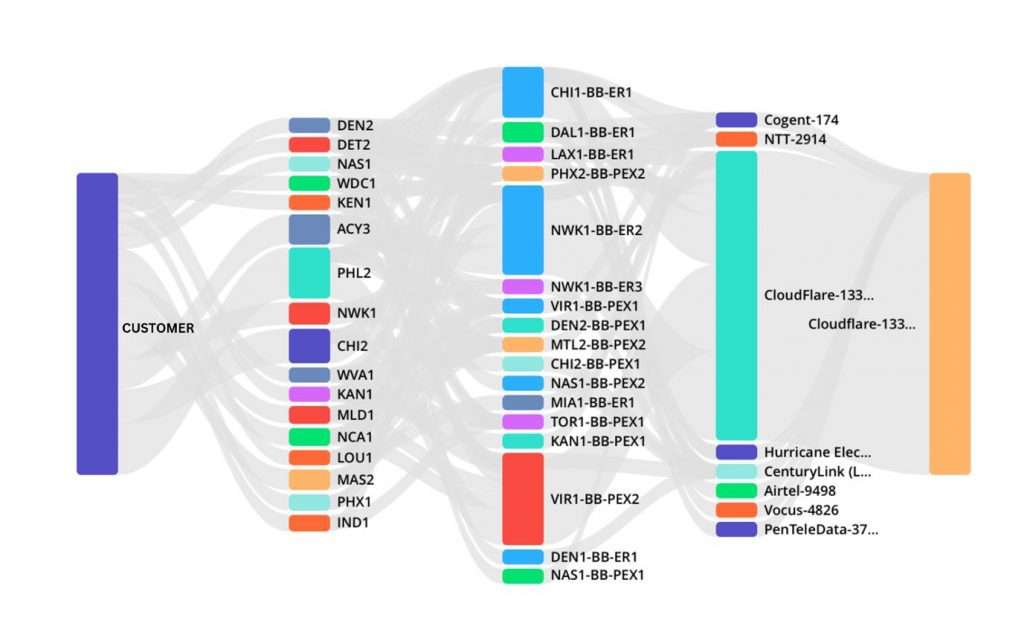
Continent 8 is no stranger to supporting high-traffic sporting contests. Whether it is annually for the Grand National or Cheltenham horse racing events in the UK and Ireland, the UEFA Champions League across Europe, March Madness in the US, or every four years for the UEFA Euro finals or FIFA World Cup, we know what it takes to ensure platform uptime.
As the partner of choice for iGaming and sports betting hosting, for both operators and suppliers alike, live in 31 US states, and supporting more than 90% of the largest brands in the marketplace (EGR US Power Rankings), we have the solutions and support systems in place that ultimately give companies the confidence they need to maximise the acquisition and retention opportunities these events present.
As standard for identified special sporting events, we:


In addition to this:
What’s key throughout is ensuring our customers are aware of all activity with notifications regularly sent such as internet and MPLS data, as well as average and maximum traffic in and out.
The Super Bowl is a huge event for sportsbooks, particularly now that the US has opened up online gambling (in varying capacity) in 31 states.
And after a very short amount of breathing space, we prepare for March Madness in the same vein!
Live in 31 states: Our expansion in the US began with a state-of-the-art data centre in Atlantic City, enabling customers to take advantage of the online sports betting market opportunities in New Jersey, while gaining immediate access to the Continent 8 global network. Today, we are live in 31 US states, with several new sites in the pipeline.
First-to-market: We have an aggressive strategy to ensure we are the first iGaming hosting provider in state, enabling our customers to capitalise on the fast-growing and competitive US iGaming and online sports betting market. Most recently, we went live in Missouri.
Regulated and compliant: We have vast regulatory experience and a dedicated compliance team, with strong regulator relationships across states, ensuring a complaint iGaming hosting solution for each.
Growing global team: We are a global team of 300+ specialists with a local presence – we ensure we have a team on the ground in the US to help you expand.
Learn more about our trusted solutions in the US here or contact the team via sales@continent8.com
The iGaming and online sports betting industry is facing unprecedented cybersecurity challenges, and multi-factor authentication (MFA) is becoming a crucial element for compliance and protection against cyber threats.

In this blog, Justin Cosnett, Chief Product Officer at Continent 8, will explore the cybersecurity landscape within iGaming, analyse the regulatory requirements for MFA in the US, discuss strategies for effectively navigating compliance while enhancing user experience and illustrate how passwordless MFA can be a game-changer in the iGaming industry.
In the rapidly expanding world of iGaming and online sports betting, cybersecurity has become a non-negotiable priority. As digital platforms proliferate, so do the threats aimed at them. Cyber criminals are constantly evolving their tactics, making it essential for operators to stay ahead of the curve. The stakes are high: a single breach can result in massive financial losses, reputational damage and erosion of customer trust.
Moreover, the nature of our industry, which involves real-time transactions and sensitive personal data, makes it an attractive target for cyber attacks. Implementing robust cybersecurity measures, including MFA, is not just about compliance; it’s about safeguarding the integrity of the gaming experience and protecting both the business and its players.
In the US, regulatory requirements for MFA vary by state.
Several regulated states have recognised the critical need for enhanced cybersecurity measures and have mandated the use of MFA for online gambling platforms. States such as Michigan, New Jersey and Pennsylvania are leading the charge – with others following suit – requiring operators to implement MFA to comply with state regulations.
These regulations are designed to protect consumers and ensure the integrity of the gaming environment. By requiring MFA, these states – and markets such as Brazil and Italy – aim to reduce the risk of unauthorised access and fraud, thereby fostering a safer and more trustworthy industry. Operators must stay informed about the regulatory landscape and ensure they meet all necessary requirements to avoid penalties and maintain their operating licenses.
Implementing MFA comes with its own set of challenges, particularly in balancing compliance with user experience. No operator wants to add friction to the login process, especially given the rise of live betting on mobile apps.
Statistics show that 20-30%* of users abandon login attempts due to friction caused by complex authentication processes. For iGaming and online sports betting operators, this can translate in a decrease in player engagement and potential profit losses of up to 20%*.
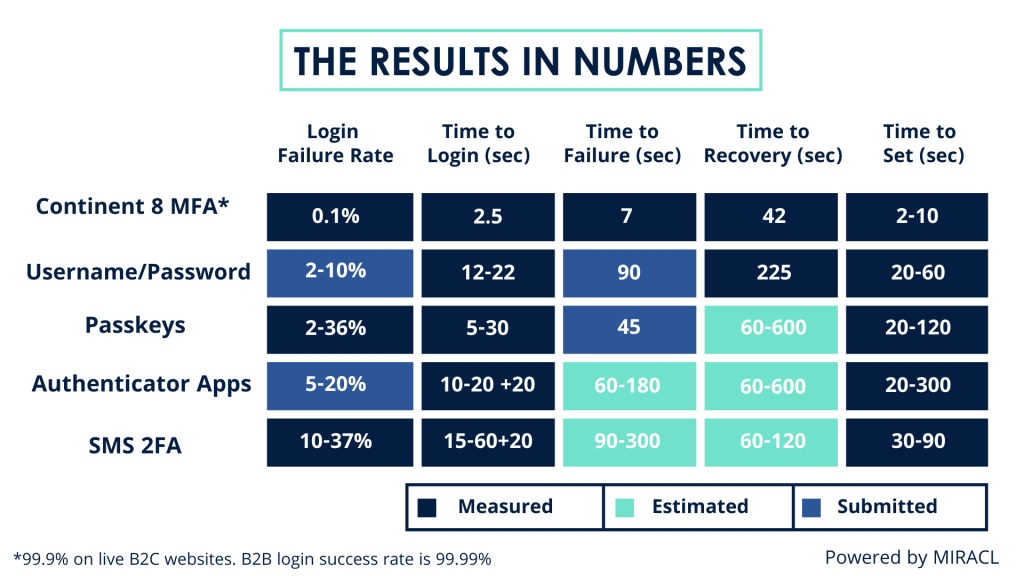
Businesses must navigate the tightrope of stringent regulatory compliance while ensuring a seamless and enjoyable user experience. This often involves investing in advanced MFA solutions that offer robust security without compromising on convenience.
Continent 8, in partnership with MIRACL, offers a cutting-edge passwordless MFA solution that addresses both security and user experience challenges. MIRACL’s technology eliminates the need for traditional passwords, replacing them with a single-step authentication process that is both secure and user-friendly.
Key statistics underscore the effectiveness of this solution: a 99.9% reduction in account takeovers, a 70% decrease in user login friction and a significant increase in user satisfaction and retention rates. By leveraging MIRACL’s passwordless authentication, operators can provide a seamless and secure login experience that meets regulatory requirements and enhances customer loyalty.
Quick. Easy. Successful.
Continent 8 is committed to supporting businesses in the iGaming and online sports betting industry with their cybersecurity needs. Our team of experts works closely with customers to design and implement a tailored MFA solution that align with regulatory requirements and business objectives.
Trust Continent 8 to be your partner in navigating the complexities of cybersecurity and regulatory compliance in the gambling industry.
Are you compliant? Are you losing players at login? Are you missing out on revenue? See a live demo of our MFA solution on our rapid-fire webinar, ‘Passwordless MFA:
Improve player login and maximise profit potential’ hosted by Justin on Monday 10 March. Register here.
Craig Lusher from our Secure team provides a comprehensive analysis of the latest Distributed Denial of Service (DDoS) statistics from the fourth quarter of the year and their implications for cybersecurity trends.
The fourth quarter of 2024 marked a significant shift in DDoS attack patterns, with 138 recorded incidents. This represents a substantial increase from 3Q’s 37 attacks, though remaining well below historical peaks like 2Q 2023’s 1,106 attacks. October emerged as the most active month, aligning with historical patterns of increased 4Q activity.
This is a trend not just at Continent 8. In fact, 4Q also happened to see the largest DDoS attack ever recorded, with Cloudflare mitigating a 5.6 (Terabits per second) Tbps Mirai-variant botnet attack on one of their customers on October 29.
4Q 2024 demonstrated interesting patterns in attack intensity:
This quarter’s largest attack of 13.4 Gbps represents a decrease from 3Q 2024’s peak of 37.0 Gbps. For perspective, this is dramatically lower than 4Q 2023’s peak of 412.9 Gbps, indicating a significant shift in attack methodologies.
Key statistics for 4Q 2024:
Key statistics for 4Q 2024:
Comparing 4Q 2024 with recent quarters reveals several interesting trends:
This shows a significant escalation in attack frequency during 4Q.
While attack frequency increased, intensity continued to decrease throughout the year.
The decrease in affected customers coupled with the dramatic increase in attacks per customer suggests a shift toward more targeted campaigns.
Comparing 4Q 2024 to 4Q 2023 shows significant changes in the threat landscape:
The higher volume but lower intensity of attacks suggests a fundamental shift in attacker strategies, focusing on persistent, lower-threshold campaigns rather than high-impact events.
The concentration of attacks on fewer customers, with more attacks per target, indicates a move toward more sophisticated, focused operations.
The shorter average attack duration (17.6 minutes) combined with increased frequency suggests a tactical shift toward ‘pulse’ style attacks rather than sustained campaigns.
While individual attack intensities have decreased significantly year-over-year, the dramatic increase in frequency and focus on specific targets suggests an evolution in threat actors’ strategies. The pattern of increased 4Q activity appears to be holding true, though manifesting differently than in previous years.
Organisations should prepare for:
Our best-in-class DDoS solution continues to evolve and in recent months we have amplified our scrubbing capacity to 5+ Tbps, as well as increased our scrubbing centres geographically deployed across multiple continents. Locations include Los Angeles, Chicago, New York, Miami, London, Amsterdam, Frankfurt, Singapore, Hong Kong and Sao Paulo.
Key features of our mitigation solution:

DDoS protection should also form part of a wider, multi-layered approach to cybersecurity. A 360-degree, end-to-end protection strategy should include DDoS mitigation solution as well as WAF/WAAP protection, MDR/EDR services, SIEM and SOC resources, VAPT assessments, backup solutions, and mobile device, phishing defence and MFA services.
This is the only way to have multiple protections in place for each attack type and to ensure the greatest level of resilience.
To learn more about how Continent 8 can help protect your organisation, contact a member of the team via sales@continent8.com or our Contact Us form.
Jerad Swimmer, Regional Sales Director at Continent 8 Technologies, explores the benefits of Vulnerability Assessment and Penetration Testing (VAPT).

Tribal casinos are experiencing substantial financial growth. As highlighted in my previous blog, 2023 was a landmark year for the tribal gaming sector, with revenues hitting a record $41.9 billion USD, as reported by the National Indian Gaming Commission. Consequently, tribal casinos are increasingly targeted by cybercriminals, with reports suggesting a nearly 60% increase in cyber attacks on tribes in 2023.
With significant financial and personal data at stake, cybersecurity in tribal gaming and casino environments is a critical priority. But where should you start? In this blog, I’ll explain why Vulnerability Assessment and Penetration Testing (VAPT) is the perfect first step to bolster tribal gaming cybersecurity.
Let’s begin by defining VAPT. Craig Lusher, our Product Principal of Secure Solutions, describes VAPT as the following:
“VAPT is defined as a comprehensive set of cybersecurity services that helps organizations identify, assess and mitigate vulnerabilities in their IT infrastructure, applications and networks. Periodic Vulnerability Assessments (VAs) scan to detect exploitable vulnerabilities in customer networks and infrastructure and record them in a register, prioritizing remedial work and demonstrating continuous improvement. Penetration Tests (PTs) use identified vulnerabilities to further exploit and gain access, testing the efficacy of preventative security measures, procedures and technology.”
By simulating real-world cyber attacks, pentesting enables tribal casino IT and cybersecurity teams to identify system weaknesses and address potential vulnerabilities before they can be exploited by malicious actors. This strategy not only strengthens the casino environment but also ensures that cybersecurity measures remain robust and adaptable to evolving threats.
VAPT aims to establish what we at Continent 8 call a “hardened cybersecurity posture.”
A hardened cybersecurity posture integrates multiple protective layers, adhering to best practices for adaptability to threats and changes. It begins with technical controls such as network segmentation, access management and encryption, complemented by active defenses including web application and API protection, intrusion detection and cybersecurity monitoring. This approach is guided by policies and procedures for incident response and risk management.
The core components of a hardened cybersecurity posture create a robust defense system. Technical controls prevent attacks, while monitoring systems identify threats. Regular assessments are conducted to uncover vulnerabilities and governance ensures consistent implementation. This comprehensive approach ensures that even if one safeguard fails, multiple other layers remain to protect assets.
Implementing VAPT protocols is a beneficial practice for any tribal gaming organization. These measures not only bolster cybersecurity but also streamline internal and external audits.
By maintaining detailed records of testing and remediation efforts, casinos can demonstrate their commitment to cybersecurity to auditors. This transparency not only aids in passing audits but also enhances the casino’s reputation as a reliable and secure establishment.
Regular penetration testing provides tribal casinos with ongoing monitoring and enhancement of cybersecurity protocols, helping them stay ahead of potential cyber threats. This ensures a safer and more secure environment for both operations and players, while also building trust with internal and external parties and stakeholders. This proactive approach, again, is vital in preserving the casino’s integrity and reputation.
When choosing penetration testing tools for tribal casino and gaming cybersecurity, select tools that offer comprehensive coverage, capable of evaluating a wide range of vulnerabilities across multiple systems and applications.
A comprehensive VAPT service should encompass the following:
For more information on VAPT or to book a meeting with me at TribalHub Cybersecurity Summit or the Indian Game Tradeshow (Booth 18), contact me at jerad.swimmer@continent8.com.
Continent 8 provides comprehensive, multi-layered threat prevention, detection and response solutions to secure your tribal organization’s digital assets in the face of evolving cyber threats. For more information on how Continent 8 can support your cybersecurity initiatives, email sales@continent.com or fill out our Contact Us page.
Also, be sure to watch the latest episode in our Tribal Talks: Cybersecurity Unlocked podcast series – also available on Spotify – to gain a deeper understanding of the technological advancements, cybersecurity challenges and best practices shaping tribal gaming landscape.
In the latest chapter of our Cultiv8 Employee Series, Jordan Holmes, Vice President of Human Resources at Continent 8 Technologies, sat down with Charlotte Barham, our Senior Manager, Group Controller located in the Isle of Man.
Throughout their conversation, Charlotte expressed her passion for numbers, her eagerness to embrace new challenges and the profound impact that Genuine Care and respect in the workplace can have in nurturing both individual and team success.

Hi Charlotte! Can you tell us a little but about yourself and your role as the Senior Manager, Group Controller at Continent 8?
Of course! I am a number-loving, hardworking, ambitious accountant with an extremely positive attitude (most of the time). I hate describing myself as an accountant as being labelled or ‘put in a box’ is a pet peeve of mine!
Born and raised on the Isle of Man, I have two step children, two dogs and a passion for staying active, making delicious food and taking on challenges, which you may have grasped already. I am thrilled to have joined Continent 8 last year as a Group Controller, where I am responsible for the production of financial reporting for all of our Group companies.
How did you come to choose a career as a Controller?
As a teenager, I was unsure of my career path but had a strong affinity for numbers, making accountancy a natural choice.
I loved the training aspect – the feeling when you passed exams and got a step closer to the goal was infectious. I finished second in the world in the year I qualified, which just shows you my enthusiasm for the field.
Upon graduation, I went from practice to industry, life assurance, and most recently, into a tech start-up. This is where I became captivated by this industry, and the opportunity at Continent 8 was one I couldn’t pass up.
What attracted you to the role and to joining the Continent 8 team? What do you enjoy most about your job?
It was the chance to really learn and be challenged again, both from a technical accountancy perspective and from working in a different environment/industry.
I love the intensity of the role, the variety of work and the amazingly supportive and equally talented people you get to meet and work with.
Can you describe some of the challenges you face as a Group Controller? How do you also stay up to date on the latest monitoring best practices and developments?
Reflecting on my first few months, the challenges really come down to the ability to support the growth of the business from a financial reporting perspective. We are making great progress in delivering timely reporting and working on continuous process improvement which will enable us to keep pace with the growth going forward.
Other challenges come from supporting the growing number of new jurisdictions and the complexities that they bring, such as recent experiences in Brazil and the Philippines in understanding tax legislation and how global businesses operate in those locations. Our own research and working with great third-party advisers ensure we are prepared and well-informed.
How do you align with Continent 8’s culture and values of Active Ownership, Purposeful Creativity and/or Genuine Care?
I believe I align well, which was a big consideration in my decision to join Continent 8. I am a huge believer that if you look after your people they will look after you. We are a service business in the tech sector, and we cannot be successful without having talented and hardworking people – Continent 8 is clearly full of them. Genuine Care and respect to people are important to me, and I strive to bring empathy, recognition and feedback to my team and colleagues daily.
Can you talk through some of the new initiatives you are or will be working on?
While ensuring the continuation of our current financial reporting projects and programmes, I’d like us to become more proactive. This includes automating and finding efficiencies in every aspect of finance!
And of course, I’ll be supporting the setup of all things finance-related in Brazil and the Philippines.
Any final thoughts?
I just wanted to say a huge thank you for the warm welcome I have had at Continent 8. I am loving it so far – my head has never been so full of new information!
With the rapid evolution of technology, robust cybersecurity is vital for enterprises to protect sensitive information and systems from a range of cyber threats, including hacking, data breaches and malware attacks. As technology advances, so do the methods used by cyber criminals, necessitating the implementation of protective cybersecurity measures.

In this blog, Craig Lusher, Product Principal of Secure Solutions at Continent 8 Technologies, explores how Security Information and Event Management (SIEM) platforms and Security Operations Centres (SOCs) allow organisations to adapt to emerging threats, maintain a robust cybersecurity posture and meet regulatory compliance.
SIEM solutions consolidate security monitoring across an organisation’s diverse technology stack, enabling SOC engineers to detect and respond to threats through a unified management interface. SIEM solutions serve as the central hub of an organisation’s security system, collecting and normalising security logs and events from various IT sources including network devices, servers and security systems. They provide a central register for all security events and logs, performing event correlation, threat enrichment and analysis, filtering out informational events and promoting true security events and threats, helping organisations protect their systems from attacks and breaches.
A SOC, or Managed Security Operations Centre (MSOC), such as those offered by Continent 8 and C8 Secure, is a dedicated team that focuses on safeguarding the company’s systems from security threats. Utilising various tools, such as a SIEM system, they watch over the company’s computer systems, spot any problems or attacks and respond to them quickly. The SOC functions as a cybersecurity team, ensuring everything is running smoothly and securely.
SIEM systems are integral in SOC cybersecurity, offering SOC teams with a holistic view of their cybersecurity events.
To begin, the SIEM system correlates and analyses the aggregated security data from internal sources and external threat intelligence to identify any unusual or suspicious activities that could indicate a potential security issue. Upon detection, it promptly alerts the SOC team, enabling them to address the issue swiftly.
In the event of an incident, the SIEM system provides comprehensive information that assists SOC analysts in understanding the nature and severity of the threat. This insight aids in effective response and helps prevent future occurrences.
Additionally, SIEM systems support compliance efforts by generating reports and maintaining logs that demonstrate the organisation’s adherence to necessary regulations. These systems are indispensable for managing security incidents and events, facilitating efficient monitoring, detection and management of security challenges by SOC teams.
Operating a SOC without a SIEM system would be quite challenging. A SIEM system provides the centralised tool required to gather and interpret security data, which is crucial for effectively preventing, detecting, investigating and responding to threats. While a SOC might use other tools and methods, SIEM systems are integral for streamlining these processes and ensuring comprehensive cybersecurity management. SIEM systems employ advanced analytics and automation to filter and prioritise security alerts, preventing the cognitive overload, or alert fatigue, that occurs when SOC engineers manually process a constant barrage of security logs. This intelligent filtering not only reduces the risk of human error and missed security events but also optimises operational costs by allowing SOC engineers to focus their expertise on critical threat analysis and incident response rather than routine log review. The result is more efficient resource allocation and enhanced security effectiveness.
A successful SIEM and SOC strategy begins with defining clear objectives and goals for each system. Essential components of effective SIEM and SOC strategies include:
Continent 8 offers a comprehensive SIEM and Managed SOC solution that addresses critical cybersecurity challenges. This platform provides centralised visibility of your entire infrastructure, coupled with 24/7 expert monitoring and rapid threat detection and response, ensuring regulatory compliance while allowing maintaining a robust cybersecurity posture.
Our SIEM and MSOC solution consists of the following key service components:
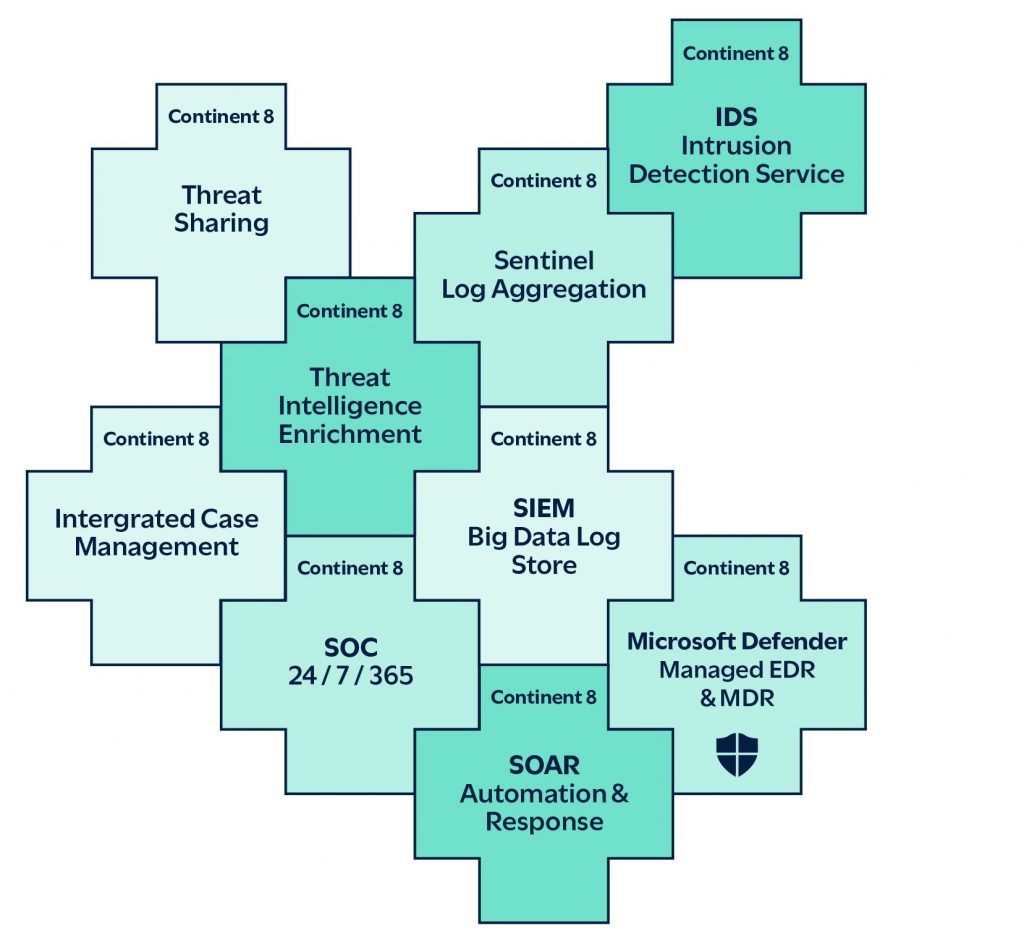
Continent 8’s SIEM platform is a comprehensive, multi-tenant solution that gathers and correlates security data across a customer’s infrastructure. Enhanced by AI-driven SOAR and correlation capabilities with integrated threat intelligence tools, it delivers advanced analytics and automated incident response workflows. The platform is built for high performance, scalability and real-time threat detection, ensuring rapid identification and resolution of security incidents.
Continent 8’s MSOC solution is a fully managed, multi-tenant service offering real-time security monitoring and incident response for customers. Following the NIST framework, it leverages our sophisticated SIEM platform to collect and analyse security alerts, offering customers actionable insights and remediation strategies through tailored playbooks. By outsourcing security operations to Managed Security Service Providers (MSSPs) such as Continent 8, customers can focus on their core business while benefiting from the expertise of Continent 8’s 24/7/365 global SOC team.
Continent 8’s Sentinel managed device is deployed within the customer’s network, aggregating logs and events from various systems, normalising them and preparing the data for secure transmission to the SIEM. It utilises encryption to ensure data integrity and privacy, compressing and deduplicating data to optimise performance. Sentinel enhances security visibility by enabling seamless data collection and forwarding.
Continent 8’s Incident Response System integrates directly into Continent 8’s SIEM to streamline incident response processes. It provides a centralised platform for managing and tracking security incidents from detection to resolution, with built-in automation for workflows and playbooks. By enabling collaborative responses and providing real-time data sharing, it significantly improves incident resolution times while enhancing post-incident analysis and reporting.
Continent 8’s Cyber Threat Intelligence Service serves as a structured repository for aggregating, analysing and sharing cyber threat intelligence. It allows organisations to collect data on threats, actors and campaigns, helping security teams anticipate and mitigate potential attacks. Through its powerful visualisation tools, the service enhances situational awareness and enables proactive threat detection.
Continent 8’s Security Orchestration and Automated Response (SOAR) tool, implemented within Continent 8’s SIEM, provides a no-code automation platform for orchestrating and automating security workflows. Its drag-and-drop interface simplifies the creation of complex incident response processes, reducing manual effort and improving efficiency. With pre-built templates and over 2,000 app integrations, it enables quick deployment of automated responses, ensuring consistent handling of security incidents.
Continent 8’s Threat Analysers and Responders are automation tools integrated into Continent 8’s SIEM that enrich security events with threat intelligence from multiple sources. With over 100 analysers, they provide critical context for observables such as IPs and URLs, supporting faster decision-making during investigations. These tools enhance threat detection and response by simplifying data analysis and improving the quality of incident responses.
Continent 8’s Intrusion Detection System (IDS), combined with our proprietary Continent 8 Sentinel platform, provides advanced network security monitoring, threat detection and response capabilities, delivering unparalleled visibility and security throughout your entire network infrastructure.
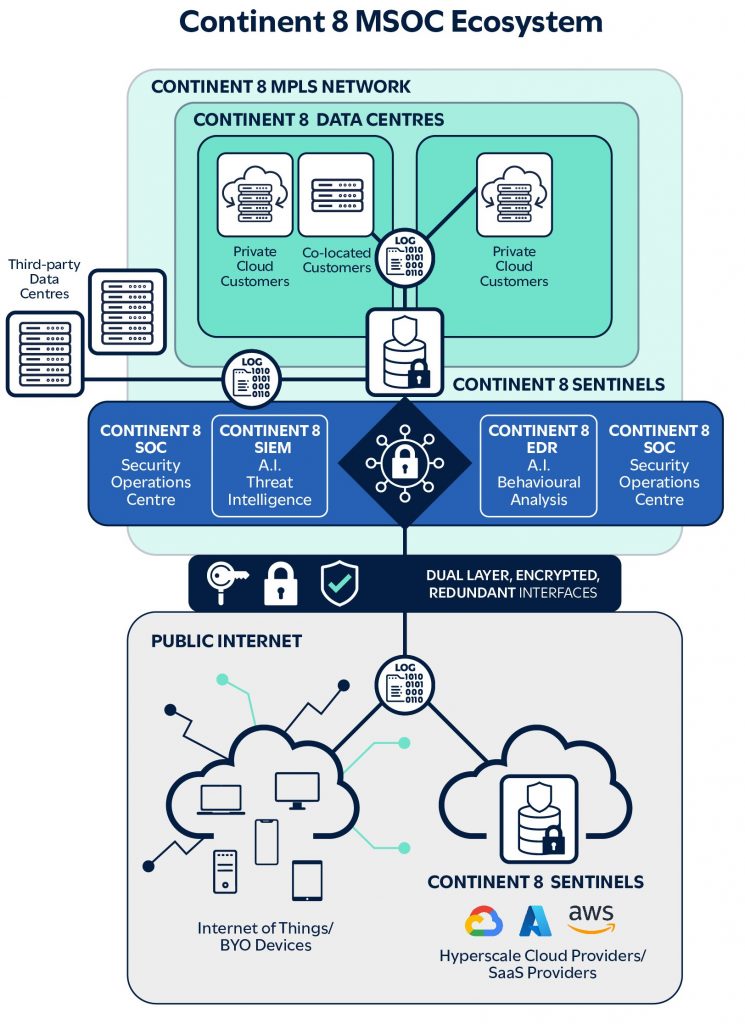
SIEM and MSOC services deliver significant cybersecurity enhancements through real-time monitoring, detection and response. This proactive approach aids in the early identification and mitigation of threats by collecting, analysing and correlating data from across a customer’s network with other ongoing security events. Collaborating with MSSPs also guarantees access to a dedicated team of SIEM and MSOC specialists who work closely with your IT team, providing playbooks and optimal risk mitigation strategies to address specific exploits or vulnerabilities, thereby ensuring optimal cybersecurity posture.
Continent 8 provides comprehensive, multi-layered threat prevention, detection and response solutions to secure your organisation’s digital assets in the face of evolving cyber threats. For more information on how Continent 8 can support your cybersecurity initiatives, email sales@continent8.com or fill out our Contact Us page.
The year 2024 marked another remarkable chapter for Continent 8 Technologies. Over the course of the year, we expanded our global network, enhanced our infrastructure and cloud services, forged new cybersecurity partnerships, introduced innovative products, launched our inaugural podcast and much more.
Explore below as we reflect on some of our remarkable accomplishments from 2024.
We continue to expand our data centre locations and points of presence globally, with an unrivalled private network of over 100 locations across four continents. Our carrier-grade network, which includes more than 35 global Internet Edge and Internet Exchange locations and over 5 Tb of IP transit capacity, provides resilient, high-performance and low-latency connectivity, ensuring zero-compromise user experiences. We’re equipped to support the growing regulated iGaming and online sports betting sector, covering more than 30 US states and six LATAM and Caribbean regions, including Brazil, an exciting new regulated market.
As the fastest go-to market supplier and the trusted infrastructure and cybersecurity partner to the industry, we power and protect the world’s leading brands, such as bet365, Apricot (formerly Microgaming), BetMGM, DraftKings, FanDuel, PointsBet, Playtech, Sportingtech and more. We also take pride in being a supporting partner to 90% of the top 10 organisations on the 2024 EGR Power 50 Rankings list and over 95% on the 2024 EGR Power US Rankings list.
We were selected to join the prestigious AWS Solution Provider Program (SPP). Through this AWS partnership, we introduced a suite of managed and professional services designed to simplify hybrid and multi-cloud environments and infrastructures. These new services, available via the AWS Marketplace, include:
This effort is part of our expanding cloud initiative designed to support the varied needs of our customers seeking hyperscale, hybrid, public and private cloud solutions.
To continue to provide the industry with comprehensive 360-degree protection, and meet the increasing market demand as a Managed Security Services Provider (MSSP) via our cybersecurity division, C8 Secure, we collaborated with cybersecurity specialists to enhance our range of cybersecurity services and solutions.
In 2024, we partnered with MIRACL, a passwordless multi-factor authentication (MFA) provider, to deliver a secure, single-step MFA solution, ensuring the most secure and efficient authentication experience possible. Additionally, we teamed up with Corrata, an advanced detection and response provider for mobile endpoints, to fortify mobile devices against modern security threats, ensuring secure access to corporate data.
As cyber threats became the new normal in 2024, it is unsurprising that we observed a record number of customers adopting our managed cybersecurity services. Sportingtech, for example, has implemented our Managed Security Operations Centre (MSOC) and Security Information and Event Management (SIEM) services to ensure continuous 24/7 monitoring, prompt threat prevention and rapid response.
In 2024, we marked a significant corporate milestone by meeting and exceeding 300 employees in December, representing a growth of over 20% from 2023. With specialists now located in 19 countries, including our newly established offices in the Philippines, we are dedicated to growing our team to deliver outstanding service and attention to our customers worldwide.

As industry leaders, we are committed to informing, educating and guiding the iGaming and online sports betting community on all matters related to infrastructure, cloud and cybersecurity. In 2024, as an engaged participant in the community, we participated in over 50 industry events, contributed to or led more than 20 industry panels and received 5 industry awards, along with numerous accolades and recognitions for our customer-centric managed services and solutions.


Our enduring presence in the iGaming industry is largely attributed to the strong partnerships we have cultivated over our 25-plus years of operation. Among these is Playtech, a leading provider of platforms, content and services in the industry. In November, we were pleased to extend our two-decades-long partnership, allowing Playtech to further utilise our range of managed and professional services. This renewal underscores both companies’ shared commitment to advancing and shaping the expanding regulated online gaming market.
Shimon Akad, COO at Playtech, stated, “Continent 8 have been our hosting and connectivity partner since the onset of our journey, 20 years ago. Renewing our agreement is a testament to the joint work and success we’ve built together, and I look forward to continuing our strong collaboration for years to come.”
At the 2024 SBC Summit North America, Michael Tobin, the Founder and CEO of Continent 8, was formally inducted into the Sports Betting Hall of Fame. He was recognised for his relentless dedication over the past 25-plus years, driving innovation and fostering growth in the global gaming industry.
Michael expressed his gratitude, sharing, “It is truly an honour to be recognised by my peers, and it’s also a testament to the hard work and dedication of the entire Continent 8 team.
“I am incredibly proud of all that we have accomplished, the value we have added to the industry and the ways in which we have empowered our customers and partners to achieve success. The iGaming and online sports betting industry is constantly evolving, and I am excited to see how we can continue to embark on this journey to grow the market together.”

Broadcom’s acquisition of VMware had a substantial impact on the HCI market. As a Nutanix Authorised Service Provider, we transitioned numerous iGaming and non-iGaming customers from their VMware ecosystems to Nutanix HCI environments. Our own documented journey from VMware’s Cloud Foundation platform to Nutanix’s Acropolis and Acropolis hypervisor (AHV) demonstrated the benefits of a VMware-to-Nutanix migration, reducing hardware infrastructure, physical footprint and operational costs, all with minimal disruption and downtime.

In response to the growing need for tailored cybersecurity services and insights within the tribal gaming sector, we launched the ‘Tribal Talks: Cybersecurity Unlocked’ podcast series. Hosted by Continent 8’s Jerad Swimmer, this podcast provides a unique forum for tribal leaders and experts to share their experiences, accomplishments and lessons learned. Through insightful discussions, listeners gain a comprehensive understanding of the technological advancements, cybersecurity challenges and best practices influencing the tribal gaming industry.

As 2024 draws to a close, we are excited to kick off the New Year with ICE 2025 (stand 2G20) in Barcelona. At ICE, we will showcase our regulatory and compliance-driven hosting, connectivity, cloud and cybersecurity solutions, with our industry experts on hand to discuss and explore the latest technological advancements, trends and challenges for 2025 and beyond.
If you’re interested in scheduling a meeting with one of our specialists or joining us for a coffee at our Caffein8 bar, please visit our ICE 2025 page.
Jerad Swimmer, Regional Sales Director at Continent 8 Technologies, explores the remarkable surge in tribal gaming revenues and its implications for cybersecurity.

The year 2023 marked a significant milestone in the tribal gaming industry, with revenues reaching an all-time high of $41.9 billion USD, according to the National Indian Gaming Commission. Advisory firm Wipfli noted that this marked the fourth consecutive year of revenue growth for tribal casinos. This remarkable growth reflects the increasing popularity and expansion of tribal casinos across the United States.
The impressive revenue figures are a testament to the hard work and innovation within the industry, highlighting the importance of tribal gaming as a vital economic driver for many tribal communities. However, with great success comes great responsibility, particularly in the realm of cybersecurity.
As tribal casinos flourish financially, they become attractive targets for cybercriminals. The surge in revenue has unfortunately been paralleled by a rise in cyber threats aimed at exploiting vulnerabilities within these establishments, with one source indicating that cyber attacks on tribes surged by almost 60% in 2023.
Cyber attacks on tribal casinos can range from data breaches to ransomware attacks, each with the potential to cause significant financial and reputational damage. The increasing sophistication of these threats demands a proactive and robust approach to cybersecurity to protect both the assets and the patrons of tribal gaming operations.
Several high-profile cybersecurity incidents have underscored the vulnerabilities within the tribal gaming sector. For instance, a tribal casino recently experienced a three-week closure due to an undisclosed cybersecurity incident. Casino officials advised previous guests to monitor their financial and credit card statements for any potential issues.
Another notable incident involved a ransomware attack that compromised all internet servers and data, with the attackers demanding up to $500,000 to restore services. These incidents highlight the critical need for enhanced cybersecurity measures to safeguard the integrity of tribal gaming enterprises.
To counter the escalating cyber threats, tribal casinos must adopt comprehensive cybersecurity strategies. This includes implementing advanced threat prevention, detection and response systems, regular security audits and continuous employee training to recognize and mitigate potential threats.
Investing in cybersecurity infrastructure, such as firewalls and mobile endpoint protection, can significantly enhance the security posture of tribal gaming operations. Collaborating with cybersecurity experts and adopting industry best practices are also pivotal steps in fortifying defenses against cyber attacks.
As cyber threats continue to evolve, tribal casinos can leverage innovative technologies and solutions to enhance their cybersecurity posture and ensure 360-degree protection. Key solutions include:
As tribal gaming continues to thrive, the critical role of cybersecurity becomes increasingly evident.
In response to the escalating threat of advanced cyber attacks targeting tribal governments and organizations, the Department of Homeland Security announced on July 1, 2024, the allocation of over $18.2 million USD in grants to 32 tribal governments. These inaugural grants, issued under the Tribal Cybersecurity Grant Program (TCGP), represent a commitment to supporting tribal communities and gaming organizations in overcoming cybersecurity challenges within their digital infrastructures and environments.
By prioritizing cybersecurity in 2025 and beyond, tribal casinos can ensure sustained growth and resilience, safeguarding their revenues and reputation in an increasingly digital world. The path forward involves a balanced approach that combines innovation and vigilance, ensuring the prosperity and longevity of the tribal gaming sector.
Continent 8 provides comprehensive, multi-layered threat prevention, detection and response solutions to secure your tribal organization’s digital assets in the face of evolving cyber threats. For more information on how Continent 8 can support your cybersecurity initiatives, email sales@continent.com or fill out our Contact Us page.
Also, be sure to watch the latest episode in our Tribal Talks: Cybersecurity Unlocked podcast series – also available on Spotify – to gain a deeper understanding of the technological advancements, cybersecurity challenges and best practices shaping tribal gaming landscape.
In the most recent installment of our Cultiv8 Employee Series, Jordan Holmes, Vice President of Human Resources at Continent 8 Technologies, engaged in a conversation with Pawel Blazejewicz, our Monitoring and Observability System Manager based in Ontario.
During the discussion, Pawel shares his unique and rewarding career path at Continent 8, his enthusiasm for big data and his team’s diverse projects and initiatives that empower both the company and our customers with robust data-driven insights, enabling smarter, more focused decision-making.
Hi Pawel! Can you tell us a little but about yourself and your role as the Monitoring Manager at Continent 8?

I have been with Continent 8 for well over a decade, taking on various roles – from System Administrator to Infrastructure Lead, Senior Cloud and Infrastructure Architect, and now my latest position, Monitoring and Observability System Manager. This project was initiated by our VP of Network, Philippe Gagne, who recognised the need to enhance our infrastructure insight amid the digitalisation wave. With Continent 8’s rapid growth driven by the opening of the US market, it’s more important than ever to leverage data not only for observability but to build an intelligent system that understands dependencies across the tens of thousands of devices comprising the complex network of IT services we provide.
How did you come to choose a career in monitoring?
I didn’t choose this role; it chose me. Our Chief Information Officer, Anthony Abou-Jaoude, recognised my passion for this project even before I did. He became my mentor for big data projects. I must say this has been a very rewarding journey, completing my IT world. Today, I am carrying the torch forward to ensure that our vision becomes reality.
What attracted you to the role and to joining the Continent 8 team? What do you enjoy most about your job?
After 12 years with this company, I’ve gained in-depth IT knowledge across all layers and levels. I’ve directed projects spanning the globe and had the opportunity to travel with them. Continent 8 has given me a place to contribute meaningfully to our future growth. In the realm of observability and metrics, I believe the key lies in digestible data that can be fed into algorithms, bringing ML and AI to life. With a deep understanding of Continent 8’s setup, I’m able to guide my team in creating a product that mirrors the real world, complete with all the dependencies and solutions we’ve built into it.
Can you describe some of the challenges you face as a Monitoring Manager? How do you also stay up to date on the latest monitoring best practices and developments?
We are creating a unique, fully customised solution tailored to Continent 8 and our valued customers’ needs. Challenges are part of the journey, but the most important aspect is surrounding yourself with people who are ready to tackle them alongside you. At Continent 8, I believe we have an incredible team ready to do just that! Remember my earlier mention of Anthony recognising me as a strong candidate to lead this project? The success of this project is a direct result of surrounding yourself with supportive people who are on the same journey, here to help and push each other forward.
They say it takes a village to raise a child – well, in this case, it takes an entire community to bring this project to fruition.
How do you align with Continent 8’s culture and values of Active Ownership, Purposeful Creativity and/or Genuine Care?
I’ve been here this long because the values the business demonstrates toward its customers align perfectly with the values I’ve shown to customers and coworkers throughout my career. As a boutique service provider, we know that listening to our customers is essential to maintaining our unique approach. A perfect example is the project I’m currently involved in – creating a comprehensive map of our entire infrastructure and services. This will not only allow us to foresee potential issues but also provide our customers with real-time data, giving them valuable insights to help their businesses grow faster and with greater focus.
Can you talk through some of the new initiatives you are or will be working on?
My main focus for the foreseeable future is to expand the amount of data we collect and to continually add more services to our observability system. By increasing our data and broadening our capabilities, we’re positioning Continent 8 to stay ahead of potential issues and empower our clients with insights that drive smarter decisions.
Any final thoughts?
If you’re interested in more detailed information about what we do, how we do it and what we offer, I invite you to explore my LinkedIn articles on our observability and monitoring system. I hope you enjoy them, and feel free to reach out if you have any questions – I’m happy to help!
To read Pawel’s “Monitoring and Observability” series, you can follow him on LinkedIn at https://www.linkedin.com/in/pawelblazejewicz.
Craig Lusher from our Secure team provides a comprehensive analysis of the latest DDoS statistics from the third quarter of the year and their implications for cybersecurity trends.
The third quarter of 2024 has continued to show relatively low DDoS attack activity, with 37 attacks recorded. This represents a slight increase from 2Q’s 32 attacks but remains significantly lower than the 359 attacks recorded in 3Q 2023. The most active month was July, which aligns with historical patterns of increased summer activity.
3Q 2024 showed some interesting patterns in attack intensity:
This quarter’s largest attack (16.8 Gbps) represents a significant decrease from 2Q 2024’s peak of 85.5 Gbps. For perspective, this is dramatically lower than the massive attacks seen in 2023, which peaked at 560.6 Gbps in Q2 2023, and over 1Tbps prior to that.
Key statistics for 3Q 2024:
Comparing 3Q 2024 with recent quarters reveals several interesting trends:
This shows a relative stabilisation at lower attack volumes compared to 2023’s numbers.
While more intense than 1Q, 3Q’s attacks remained relatively moderate compared to historical peaks.
The consistent number of affected customers over 2Q and 3Q 2024 suggests a stable threat landscape, though individual customers faced more repeated attacks in 3Q.
Comparing 3Q 2024 to 3Q 2023 shows a dramatic shift in the threat landscape:
The lower volume but moderate intensity of attacks suggests a shift in attacker strategies, possibly focusing on more targeted, strategic attacks rather than broad campaigns.
The average attack duration of 2 hours shows a trend toward longer, more sustained attacks compared to previous quarters, potentially indicating more sophisticated attack strategies.
While attack volumes remain relatively low compared to 2023 and previous, the increase in attacks per individual customer and attack duration suggests continued evolution in threat actors’ strategies. Organisations should maintain robust DDoS protection despite the lower overall attack volumes, as the pattern of attacks suggests more targeted and potentially more sophisticated approaches.
The historical pattern of increased activity during major sporting events and holiday periods suggests potential for increased activity in the upcoming quarters, particularly with various significant events on the horizon.
This analysis demonstrates the importance of maintaining comprehensive DDoS protection and the value of Continent 8’s multi-layered security approach, even during periods of relatively low attack volume.
Our best-in-class DDoS solution continues to evolve and in recent months we have amplified our scrubbing capacity to 5+ Tbps, as well as increased our scrubbing centres geographically deployed across multiple continents. Locations include Los Angeles, Chicago, New York, Miami, London, Amsterdam, Frankfurt, Singapore, Hong Kong and Sao Paulo.
Key features of our mitigation solution:

DDoS protection should also form part of a wider, multi-layered approach to cybersecurity. A 360-degree, end-to-end protection strategy should include DDoS mitigation solution as well as WAF/WAAP protection, MDR/EDR services, SIEM and SOC resources, VAPT assessments, backup solutions, and mobile device and phishing defence services.
This is the only way to have multiple protections in place for each attack type and to ensure the greatest level of resilience.
To learn more about how Continent 8 can help protect your organisation, contact a member of the team via sales@continent8.com or our Contact Us form.